In the era of Quality 4.0, cloud cybersecurity has become a crucial concern for businesses. Many companies are exploring the impact of switching from on-premise Quality Management Systems (QMS) to cloud-based QMS. It is important to understand the differences between these two types of QMS. In this article, we will begin by identifying the key differences between a cloud-based QMS and an on-premise solution and then delve into the essential aspects of cybersecurity that you need to consider while planning your switch.
A cloud-based QMS vs. an on-premise solution
With the rapid adoption of cloud-based technologies, companies now have the choice to opt for cloud-based QMS, unlike the olden days when the only option was on-premise QMS. Both options have their pros and cons, and to know the best choice, you must understand both sides of the coin. To help you make an informed decision we have stipulated some key differences between a cloud-based QMS and an on-premise solution.
Cloud-based QMS
When your vendor provides QMS Software as a Service by hosting, maintaining, and updating your software on a cloud platform you have a cloud-based QMS.
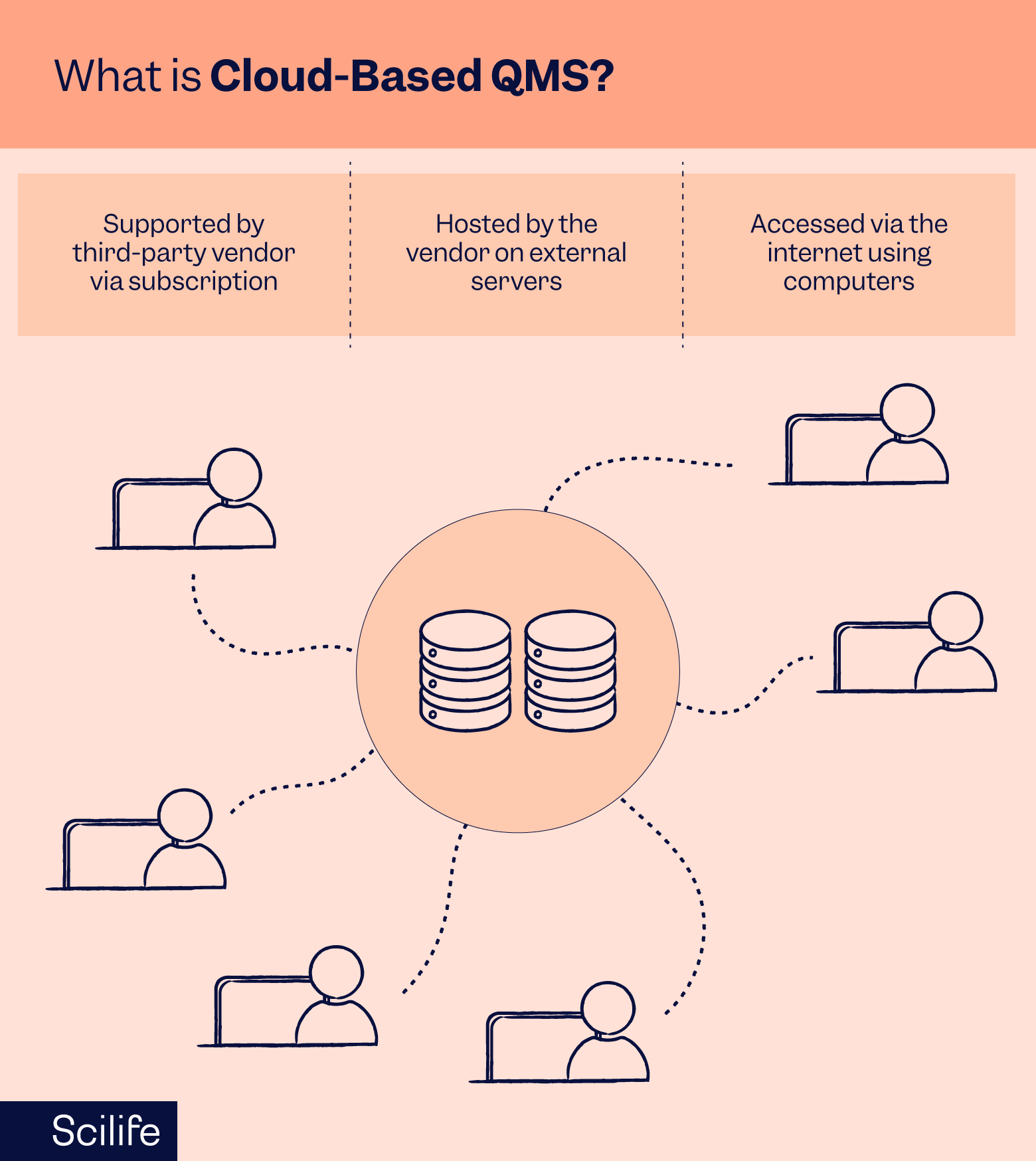
- Accessing a cloud-based QMS: These applications are accessible over the internet in the form of a website. You can access them on your mobile or laptop from anywhere in the world.
- Infrastructure expense for cloud-based QMS: You do not need a desktop installation, a dedicated server, in-house IT infrastructure, and an IT team to host, maintain, and update the software.
- Payment terms for cloud-based QMS: You only pay monthly or annual charges to your vendor that cover charges for the server, network, maintenance, and upgrades. Your charges are mainly based on the number of users, therefore your subscription charges may vary depending on the number of users in that month or year.
- Cybersecurity of cloud-based QMS: Cloud-based QMS is a service-based model where you are letting an expert vendor take care of your risks and costs associated with the QMS software. This means that you will own your QMS data but the data security, compliance, and audit capabilities will be outsourced to the cloud provider.
- Accounting of expenses for cloud-based QMS: The expenses incurred on a cloud-based QMS will be accounted as your company’s operational expenses.
On-premise QMS
You have an on-premise QMS if your vendor sells their legacy QMS software in exchange for a one-time license fee, but you will be responsible for hardware and network resources. A QMS on-premises includes all of the network infrastructure, data center, power, and cooling equipment, servers, operating systems, and databases.
- Accessing an on-premise QMS: An on-premise QMS typically requires an installation on your personal computer and can not be accessed outside your organization’s network.
- Infrastructure expense for on-premise QMS: In addition to the initial investment in hardware and network resources, you will eventually also incur lifetime maintenance expenses for hardware updates, expansions, security patching, troubleshooting, and more.
- Payment terms for on-premise QMS: In the traditional licensing model, you only pay once for buying the software usage rights. However in this case, you will still need to pay the vendor annually for additional support, and maintenance, and you may also not have automatic access to the latest version of the software without additional purchase.
- Cybersecurity of on-premise QMS: Unlike in the case of cloud-based QMS, in on-premise QMS software, you are responsible for all the risks and costs associated with the QMS software. But it also means that you have 100% control over your data.
- Accounting of expenses for cloud-based QMS: The expenses incurred on account of on-premise software will appear on your company’s capital expenditure.
Cybersecurity: the deal breaker
As much as the choice between a cloud-based QMS and an on-premise solution depends on your organization’s IT infrastructure and purchasing capacity, it also depends on another uncompromising factor, Cybersecurity. Cybersecurity is non-negotiable for every organization irrespective of the size and scale of its operations. That’s why we say cybersecurity is the clear deal breaker here.
Although on a superficial level, you may conclude that on-premise solutions will provide the best cybersecurity, that’s not true. Surprised by the previous statement? Then let’s delve deeper to understand why a cloud-based QMS software offers better cybersecurity than an on-premise solution.
Challenges of an on-premise solution in terms of cybersecurity
In an on-premise solution, the data is stored locally. Considering the strict regulations around data integrity you will need to ensure stricter controls for accessing, modifying, and deleting data. Additionally, you will be required to maintain audit trails. The onus of proving data integrity compliance is entirely on you. As you have the data, during an audit you will possibly face more scrutiny on the data integrity aspect than a competitor who has a cloud-based QMS.
Additionally, in a traditional licensing system, you are required to customize your software for implementation. Customizable software falls under GAMP Category 5 which is associated with the highest risks in all GAMP categories. Therefore, you may need to take more Computer System Validation steps to ensure GxP compliance to implement an on-premise solution.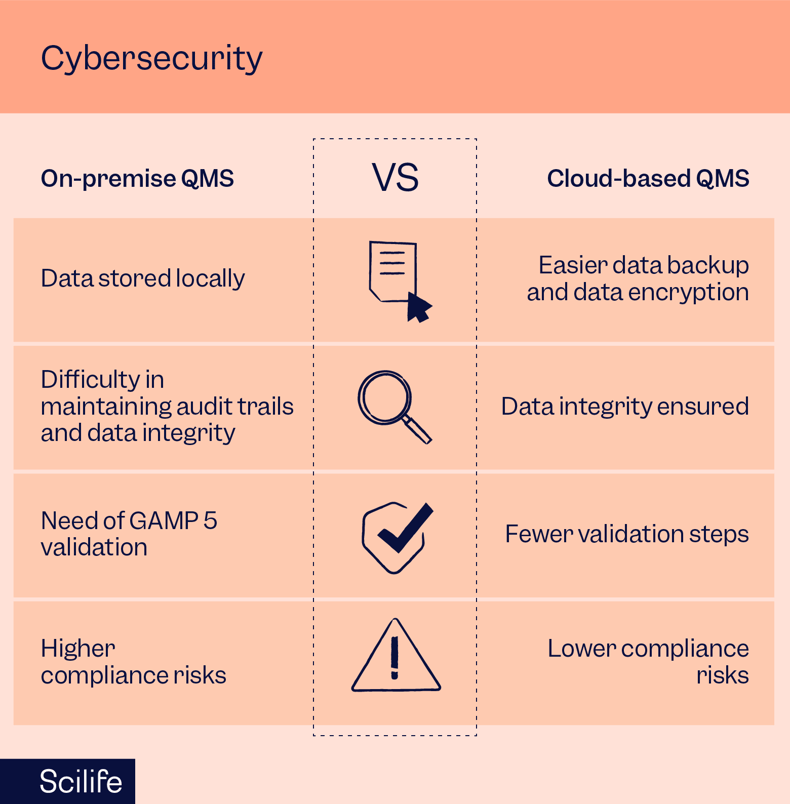
Benefits of a cloud-based QMS regarding cybersecurity
The myth about higher risks in cloud cybersecurity is outdated. In a cloud-based QMS, your data is stored remotely on a vendor platform/ third-party platform. Therefore, the responsibility of managing the data in intact form lies with the vendor/ third-party platform. Of course, you need to do due diligence to confirm that the vendor/third party is capable of complying with data integrity regulations, and also has a solid disaster recovery plan to protect your data.
The key players in cloud platform service players such as Amazon, Microsoft Azure, Google, etc., have highly skilled data engineers and professionals who can manage data backups and recovery with much more efficiency than a small in-house IT team. Over the years these key players have also built large infrastructures to protect and secure your data. Your service provider can also take additional measures such as data encryption, and multi-factor authentication to protect your data on your behalf.
This gives you the advantage of not having to invest in resources for managing data integrity. Additionally, as the data is hosted on remote servers that are inaccessible and unknown to your employees, there is no way to tamper with the data.
In contrast to the on-premise solution, cloud-based systems fall under the category of non-configurable (Category 3) or configurable category (Category 4) of the GAMP guideline. Therefore, you will need to execute fewer computer system validation steps to comply with GAMP guidelines.
Cybersecurity of Scilife’s Cloud-based QMS
At Scilife, safeguarding your information is our top priority. We've implemented multiple layers of protection to keep your data secure.
Firstly, we've set up a Web application firewall on our Application Load Balancer. This firewall acts as a gatekeeper, monitoring incoming traffic and blocking any unauthorized access attempts. It's equipped with intelligent rules that we've carefully crafted to detect suspicious activity. For example, if we notice repeated requests from the same IP address, we may prompt the user to verify their identity with a CAPTCHA. Additionally, we ensure that all requests come from valid host URLs, not just IP addresses, adding an extra layer of security.
Furthermore, on the application level, we've implemented proactive measures to thwart potential threats. If there are five consecutive failed login attempts, we temporarily block the account to prevent further unauthorized access attempts. For more serious breaches, such as ten failed attempts, we take immediate action by permanently blocking the account to safeguard your data from any malicious activity.
Rest assured, we're constantly monitoring and updating our security protocols to stay ahead of any potential threats and keep your information safe and secure.
Conclusion
In conclusion, when choosing between a cloud-based QMS and an on-premise solution, cybersecurity is a deal breaker. With advanced infrastructure, skilled IT professionals, and years of experience, the cloud platform service providers are better equipped to deal with cybersecurity threats. Additionally, the remote location of the data adds another layer of security to the data.
It is also important to consider that as per GAMP 5 guidelines, on-premise solutions require more steps for computer system validation due to increased risks associated with customizable software. On the other hand, being non-configurable or configurable software, cloud-based QMS requires fewer steps for computer system validation.
Finally, considering lower infrastructure investments and lower compliance risk, cloud-based QMS has a definite edge over traditional on-premise QMS.
Read more about Scilife smart QMS protects and safeguards your data.